Here's a nice Cisco guide and use case scenarios for deploying Cisco ASAv in Microsoft Azure Cloud. You usually connect your on-premise infrastructure into a public cloud (now becomes a hybrid cloud) via a VPN gateway or deploy a virtual firewall from a third party vendor.
To deploy a Cisco ASAv, create a Resource.
In Azure Marketplace, type/search for Cisco ASAv
Select Cisco Adaptive Security Appliance virtual (ASAv).
Click Create.
Select Subscription: Azure subscription 1 > Resource group > Create new > type a Name: az-lab-rg (create a Resource name that make sense to you) > click OK.
Select a Region: Southeast Asia (since I'm in Singapore) > type Virtual Machine name: az-asav-1 > select Software Version: 9.14.1.10 (default) > type Username: cisco-admin > type Password (must be long and complex) > type password again to confirm > click Next: Cisco ASAv settings
Skip and leave the default settings for Virtual machine size and Storage account.
Under Public IP address > Create new.
Skip and leave the default settings for Public IP address and DNS label.
Under Virtual network > click Create new.
You can change the Name and Address Space for the Virtual network (vnet).
The Subnet Address range must be in Classless Inter-Domain Routing (CIDR) notation > click OK.
The ASAv is assigned with 4 virtual networks/NIC. Assign each virtual network with a subnet.
Click Review + create.
Validation will take just a few seconds to finish.
Click Create to deploy the ASAv.
The deployment might take a few minutes to finish (mine took around 5 mins).
Click Go to Resource group.
Click az-asav-1 (Virtual machine).
Notice a public IP address has been assigned.
The first virtual network (Nic0) has the public IP assigned.
It also has an internal/Private IP address 10.10.1.4 (subnet1).
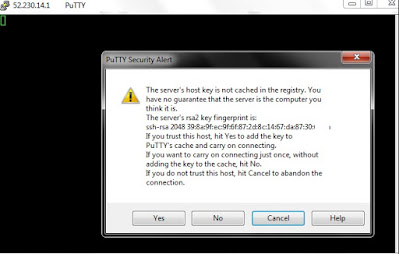
SSH to the assigned public IP address.
Click Yes to Continue.
Type the user and password created earlier.
Type enable to access privilege exec mode (#) and enter the enable password.
Below are some ASA show command output.
az-asav-1# show version
Cisco Adaptive Security Appliance Software Version 9.14(1)10
SSP Operating System Version 2.8(1.108)
Device Manager Version 7.14(1)
Compiled on Tue 19-May-20 09:14 PDT by builders
System image file is "boot:/asa9141-10-smp-k8.bin"
Config file at boot was "startup-config"
az-asav-1 up 12 mins 44 secs
Hardware: ASAv, 14336 MB RAM, CPU Xeon E5 series 2300 MHz, 1 CPU (4 cores)
Internal ATA Compact Flash, 9216MB
Slot 1: ATA Compact Flash, 9216MB
BIOS Flash Firmware Hub @ 0x0, 0KB
0: Ext: Management0/0 : address is 0022.4856.23e0, irq 0
1: Ext: GigabitEthernet0/0 : address is 0022.4856.226b, irq 0
2: Ext: GigabitEthernet0/1 : address is 0022.4856.2394, irq 0
3: Ext: GigabitEthernet0/2 : address is 0022.4856.289d, irq 0
4: Int: Internal-Data0/0 : address is 0000.0100.0001, irq 0
License mode: Smart Licensing
ASAv Platform License State: Unlicensed
No active entitlement: no feature tier and no throughput level configured
Firewall throughput limited to 100 Kbps
Licensed features for this platform:
Maximum VLANs : 200
Inside Hosts : Unlimited
Failover : Active/Active
Encryption-DES : Enabled
Encryption-3DES-AES : Enabled
Security Contexts : 2
Carrier : Disabled
AnyConnect Premium Peers : 2
AnyConnect Essentials : Disabled
Other VPN Peers : 750
Total VPN Peers : 750
AnyConnect for Mobile : Disabled
AnyConnect for Cisco VPN Phone : Disabled
Advanced Endpoint Assessment : Disabled
Shared License : Disabled
Total TLS Proxy Sessions : 2
Botnet Traffic Filter : Enabled
Cluster : Disabled
Serial Number: 9ARGEGM1234
Image type : Release
Key version : A
Configuration last modified by cisco-admin at 10:11:09.399 UTC Wed Aug 26 2020
az-asav-1# show interface ip brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 unassigned YES unset administratively down up
GigabitEthernet0/1 unassigned YES unset administratively down up
GigabitEthernet0/2 unassigned YES unset administratively down up
Internal-Data0/0 169.254.1.1 YES unset up up
Management0/0 10.10.1.4 YES DHCP up up
az-asav-1# sh run
: Saved
:
: Serial Number: 9ARGEGMAHSG
: Hardware: ASAv, 14336 MB RAM, CPU Xeon E5 series 2300 MHz, 1 CPU (4 cores)
:
ASA Version 9.14(1)10
!
hostname az-asav-1
enable password ***** pbkdf2
service-module 0 keepalive-timeout 4
service-module 0 keepalive-counter 6
names
no mac-address auto
!
interface GigabitEthernet0/0
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
no management-only
nameif management
security-level 0
ip address dhcp setroute
!
ftp mode passive
dns domain-lookup management
dns server-group DefaultDNS
name-server 168.63.129.16
pager lines 23
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
no snmp-server location
no snmp-server contact
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpool policy
auto-import
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 0509
308205b7 3082039f a0030201 02020205 09300d06 092a8648 86f70d01 01050500
3045310b 30090603 55040613 02424d31 19301706 0355040a 13105175 6f566164
6973204c 696d6974 6564311b 30190603 55040313 1251756f 56616469 7320526f
6f742043 41203230 1e170d30 36313132 34313832 3730305a 170d3331 31313234
31383233 33335a30 45310b30 09060355 04061302 424d3119 30170603 55040a13
1051756f 56616469 73204c69 6d697465 64311b30 19060355 04031312 51756f56
61646973 20526f6f 74204341 20323082 0222300d 06092a86 4886f70d 01010105
00038202 0f003082 020a0282 0201009a 18ca4b94 0d002daf 03298af0 0f81c8ae
4c19851d 089fab29 4485f32f 81ad321e 9046bfa3 86261a1e fe7e1c18 3a5c9c60
172a3a74 8333307d 615411cb edabe0e6 d2a27ef5 6b6f18b7 0a0b2dfd e93eef0a
c6b310e9 dcc24617 f85dfda4 daff9e49 5a9ce633 e62496f7 3fba5b2b 1c7a35c2
d667feab 66508b6d 28602bef d760c3c7 93bc8d36 91f37ff8 db1113c4 9c7776c1
aeb7026a 817aa945 83e205e6 b956c194 378f4871 6322ec17 6507958a 4bdf8fc6
5a0ae5b0 e35f5e6b 11ab0cf9 85eb44e9 f80473f2 e9fe5c98 8cf573af 6bb47ecd
d45c022b 4c39e1b2 95952d42 87d7d5b3 9043b76c 13f1dedd f6c4f889 3fd175f5
92c391d5 8a88d090 ecdc6dde 89c26571 968b0d03 fd9cbf5b 16ac92db eafe797c
adebaff7 16cbdbcd 252be51f fb9a9fe2 51cc3a53 0c48e60e bdc9b476 0652e611
13857263 0304e004 362b2019 02e874a7 1fb6c956 66f07525 dc67c10e 616088b3
3ed1a8fc a3da1db0 d1b12354 df44766d ed41d8c1 b222b653 1cdf351d dca1772a
31e42df5 e5e5dbc8 e0ffe580 d70b63a0 ff33a10f ba2c1515 ea97b3d2 a2b5bef2
8c961e1a 8f1d6ca4 6137b986 7333d797 969e237d 82a44c81 e2a1d1ba 675f9507
a32711ee 16107bbc 454a4cb2 04d2abef d5fd0c51 ce506a08 31f991da 0c8f645c
03c33a8b 203f6e8d 673d3ad6 fe7d5b88 c95efbcc 61dc8b33 77d34432 35096204
921610d8 9e2747fb 3b21e3f8 eb1d5b02 03010001 a381b030 81ad300f 0603551d
130101ff 04053003 0101ff30 0b060355 1d0f0404 03020106 301d0603 551d0e04
1604141a 8462bc48 4c332504 d4eed0f6 03c41946 d1946b30 6e060355 1d230467
30658014 1a8462bc 484c3325 04d4eed0 f603c419 46d1946b a149a447 3045310b
30090603 55040613 02424d31 19301706 0355040a 13105175 6f566164 6973204c
696d6974 6564311b 30190603 55040313 1251756f 56616469 7320526f 6f742043
41203282 02050930 0d06092a 864886f7 0d010105 05000382 0201003e 0a164d9f
065ba8ae 715d2f05 2f67e613 4583c436 f6f3c026 0c0db547 645df8b4 72c946a5
03182755 89787d76 ea963480 1720dce7 83f88dfc 07b8da5f 4d2e67b2 84fdd944
fc775081 e67cb4c9 0d0b7253 f8760707 4147960c fbe08226 93558cfe 221f6065
7c5fe726 b3f73290 9850d437 7155f692 2178f795 79faf82d 26876656 3077a637
78335210 58ae3f61 8ef26ab1 ef187e4a 5963ca8d a256d5a7 2fbc561f cf39c1e2
fb0aa815 2c7d4d7a 63c66c97 443cd26f c34a170a f890d257 a21951a5 2d9741da
074fa950 da908d94 46e13ef0 94fd1000 38f53be8 40e1b46e 561a20cc 6f588ded
2e458fd6 e9933fe7 b12cdf3a d6228cdc 84bb226f d0f8e4c6 39e90488 3cc3baeb
557a6d80 9924f56c 01fbf897 b0945beb fdd26ff1 77680d35 6423acb8 55a103d1
4d4219dc f8755956 a3f9a849 79f8af0e b911a07c b76aed34 d0b62662 381a870c
f8e8fd2e d3907f07 912a1dd6 7e5c8583 99b03808 3fe95ef9 3507e4c9 626e577f
a75095f7 bac89be6 8ea201c5 d666bf79 61f33c1c e1b9825c 5da0c3e9 d848bd19
a2111419 6eb2861b 683e4837 1a88b75d 965e9cc7 ef276208 e291195c d2f121dd
ba174282 97718153 31a99ff6 7d62bf72 e1a3931d cc8a265a 0938d0ce d70d8016
b478a53a 874c8d8a a5d54697 f22c10b9 bc5422c0 01506943 9ef4b2ef 6df8ecda
f1e3b1ef df918f54 2a0b25c1 2619c452 100565d5 8210eac2 31cd2e
quit
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 60
ssh version 2
ssh key-exchange group dh-group14-sha256
ssh 0.0.0.0 0.0.0.0 management
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
username cisco-admin password ***** pbkdf2 privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect snmp
!
service-policy global_policy global
prompt hostname context
call-home reporting anonymous prompt 2
call-home
profile License
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination transport-method http
Cryptochecksum:a9c0ad8ffa363d39b14d06fc53c84ce6
: end
To stop a Virtual machine, click on the specific Virtual machine > Stop > OK.
Notice the public IP address will be lost since a Dynamic IP assignment was chosen instead of Static IP.
Stopping a VM took a few of minutes to finish.
Go to Activity log.































No comments:
Post a Comment