The Cisco DevNet Sandbox is a free online tool where you can test and develop various Cisco technologies, i.e. Cloud, Security, SD WAN, etc. without owning or setup any Cisco hardware or virtual server. You just register or use your existing CCO login.
There are a lot of Sandbox virtual labs to choose from. This is useful if you need to test a new IOS-XE or NX-OS feature without blowing up your production network. You can also do a Proof of Concept (POC) or Proof of Value (POV) without having to ask from your Cisco Account Manager for a loan hardware. It's also a great learning tool for those studying their Cisco certifications, i.e. CCNA, CCNP, etc.
Click a specific Sandbox Lab. In this case I chose the Cisco Modeling Labs (CML) Enterprise > click Reserve.
The Sandbox lab setup takes around 10 minutes to complete. You can check the time left on the Setup green icon on the top right corner. You'll receive an email about the Sandbox lab chosen and a download link for the Cisco AnyConnect VPN client software installer. I used Cisco AnyConnect version 4.x in my laptop.
Once the Setup is finished, the Sandbox Setup changed to Active (top right) and nodes will have a green dot. You'll also receive another email informing the Sandbox lab is ready and gives you a temporary username/password login.
Copy/paste the AnyConnect VPN address/URL > click Connect > type the username and password provided in the email.
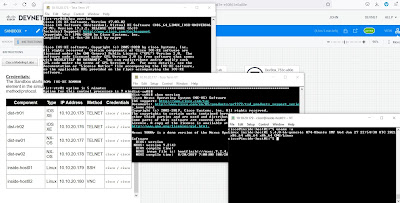
Open an SSH client > select the Service: Telnet > type the Sandbox component IP address > click OK. I used TeraTerm in this case.
There's also a PDF network diagram you can view or download in the Instructions section.
dist-rtr01#show version
Cisco IOS XE Software, Version 17.03.02
Cisco IOS Software [Amsterdam], Virtual XE Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 17.3.2, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2020 by Cisco Systems, Inc.
Compiled Sat 31-Oct-20 13:16 by mcpre
Cisco IOS-XE software, Copyright (c) 2005-2020 by cisco Systems, Inc.
All rights reserved. Certain components of Cisco IOS-XE software are
licensed under the GNU General Public License ("GPL") Version 2.0. The
software code licensed under GPL Version 2.0 is free software that comes
with ABSOLUTELY NO WARRANTY. You can redistribute and/or modify such
GPL code under the terms of GPL Version 2.0. For more details, see the
documentation or "License Notice" file accompanying the IOS-XE software,
or the applicable URL provided on the flyer accompanying the IOS-XE
software.
ROM: IOS-XE ROMMON
dist-rtr01 uptime is 5 minutes
Uptime for this control processor is 7 minutes
System returned to ROM by reload
System image file is "bootflash:packages.conf"
Last reload reason: factory-reset
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
export@cisco.com.
License Level: ax
License Type: N/A(Smart License Enabled)
Next reload license Level: ax
The current throughput level is 1000 kbps
Smart Licensing Status: UNREGISTERED/No Licenses in Use
cisco CSR1000V (VXE) processor (revision VXE) with 1105351K/3075K bytes of memory.
Processor board ID 9LFWOLT44MQ
Router operating mode: Autonomous
6 Gigabit Ethernet interfaces
32768K bytes of non-volatile configuration memory.
3012036K bytes of physical memory.
6188032K bytes of virtual hard disk at bootflash:.
Configuration register is 0x2102
dist-rtr01#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 10.10.20.175 YES TFTP up up
GigabitEthernet2 172.16.252.21 YES TFTP up up
GigabitEthernet3 172.16.252.25 YES TFTP up up
GigabitEthernet4 172.16.252.2 YES TFTP up up
GigabitEthernet5 172.16.252.10 YES TFTP up up
GigabitEthernet6 172.16.252.17 YES TFTP up up
Loopback0 unassigned YES unset administratively down down
dist-rtr01#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 19 subnets, 3 masks
O 172.16.101.0/24 [110/41] via 172.16.252.9, 00:07:16, GigabitEthernet5
[110/41] via 172.16.252.1, 00:09:37, GigabitEthernet4
O 172.16.102.0/24 [110/41] via 172.16.252.9, 00:09:26, GigabitEthernet5
[110/41] via 172.16.252.1, 00:07:16, GigabitEthernet4
O 172.16.103.0/24 [110/41] via 172.16.252.9, 00:07:11, GigabitEthernet5
[110/41] via 172.16.252.1, 00:07:16, GigabitEthernet4
O 172.16.104.0/24 [110/41] via 172.16.252.9, 00:07:11, GigabitEthernet5
[110/41] via 172.16.252.1, 00:07:16, GigabitEthernet4
O 172.16.105.0/24 [110/41] via 172.16.252.9, 00:07:11, GigabitEthernet5
[110/41] via 172.16.252.1, 00:07:16, GigabitEthernet4
C 172.16.252.0/30 is directly connected, GigabitEthernet4
L 172.16.252.2/32 is directly connected, GigabitEthernet4
O 172.16.252.4/30 [110/2] via 172.16.252.18, 00:11:04, GigabitEthernet6
C 172.16.252.8/30 is directly connected, GigabitEthernet5
L 172.16.252.10/32 is directly connected, GigabitEthernet5
O 172.16.252.12/30
[110/2] via 172.16.252.18, 00:11:04, GigabitEthernet6
C 172.16.252.16/30 is directly connected, GigabitEthernet6
L 172.16.252.17/32 is directly connected, GigabitEthernet6
C 172.16.252.20/30 is directly connected, GigabitEthernet2
L 172.16.252.21/32 is directly connected, GigabitEthernet2
C 172.16.252.24/30 is directly connected, GigabitEthernet3
L 172.16.252.25/32 is directly connected, GigabitEthernet3
O 172.16.252.28/30
[110/2] via 172.16.252.18, 00:11:04, GigabitEthernet6
O 172.16.252.32/30
[110/2] via 172.16.252.18, 00:11:04, GigabitEthernet6
Once you're finished, click End (stop hand icon on top right).
To clear the cached VPN address, go to Cisco AnyConnect Security Mobility Client folder:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client
Select preferences_global (an XML file) > delete.
You can verify the content of the XML file by opening it in Notepad. Notice it has the Cisco Sandbox URL and public IP address.
















No comments:
Post a Comment